How To Find If Keylogger Is Installed On Computer
Keyloggers: Implementing keyloggers in Windows. Office Two
In February 2005, Joe Lopez, a businessman from Florida, filed a conform confronting Bank of America after unknown hackers stole $90,000 from his Bank of America account. The money had been transferred to Latvia.
An investigation showed that Mr. Lopez's calculator was infected with a malicious plan, Backdoor.Coreflood, which records every keystroke and sends this information to malicious users via the Internet. This is how the hackers got hold of Joe Lopez'south user proper noun and countersign, since Mr. Lopez often used the Internet to manage his Banking company of America business relationship.
However the court did non rule in favor of the plaintiff, saying that Mr. Lopez had neglected to take basic precautions when managing his banking company account on the Cyberspace: a signature for the malicious code that was found on his organisation had been added to nearly all antivirus production databases back in 2003.
Joe Lopez'southward losses were caused past a combination of overall carelessness and an ordinary keylogging program.
About Keyloggers
The term 'keylogger' itself is neutral, and the word describes the programme's role. Most sources define a keylogger equally a software program designed to secretly monitor and log all keystrokes. This definition is not altogether correct, since a keylogger doesn't have to be software – it can too be a device. Keylogging devices are much rarer than keylogging software, simply it is important to keep their existence in mind when thinking about data security.
Legitimate programs may have a keylogging function which can exist used to call certain program functions using "hotkeys," or to toggle between keyboard layouts (e.g. Keyboard Ninja). In that location is a lot of legitimate software which is designed to let administrators to track what employees do throughout the day, or to permit users to runway the action of 3rd parties on their computers. Notwithstanding, the ethical boundary between justified monitoring and espionage is a fine line. Legitimate software is oftentimes used deliberately to steal confidential user information such as passwords.
Most modernistic keyloggers are considered to be legitimate software or hardware and are sold on the open market. Developers and vendors offer a long list of cases in which it would be legal and appropriate to employ keyloggers, including:
- Parental control: parents tin track what their children do on the Internet, and can opt to be notified if there are any attempts to access websites containing adult or otherwise inappropriate content;
- Jealous spouses or partners tin use a keylogger to rail the actions of their amend half on the Internet if they suspect them of "virtual cheating";
- Company security: tracking the employ of computers for non-work-related purposes, or the use of workstations later hours;
- Visitor security: using keyloggers to track the input of key words and phrases associated with commercial information which could damage the company (materially or otherwise) if disclosed;
- Other security (e.g. law enforcement): using keylogger records to clarify and rails incidents linked to the utilize of personal computers;
- Other reasons.
Nevertheless, the justifications listed higher up are more subjective than objective; the situations can all be resolved using other methods. Additionally, whatsoever legitimate keylogging program can however be used with malicious or criminal intent. Today, keyloggers are mainly used to steal user information relating to various online payment systems, and virus writers are constantly writing new keylogger Trojans for this very purpose.
Furthermore, many keyloggers hide themselves in the system (i.eastward. they accept rootkit functionality), which makes them fully-fledged Trojan programs.
As such programs are extensively used past cyber criminals, detecting them is a priority for antivirus companies. Kaspersky Lab's malware nomenclature system has a defended category for malicious programs with keylogging functionality: Trojan-Spy. Trojan-Spy programs, as the name suggests, rail user activity, relieve the information to the user's difficult deejay and then frontward it to the writer or 'master' of the Trojan. The information nerveless includes keystrokes and screen-shots, used in the theft of banking data to support online fraud.
Why keyloggers are a threat
Unlike other types of malicious program, keyloggers present no threat to the system itself. Nevertheless, they can pose a serious threat to users, every bit they tin can be used to intercept passwords and other confidential data entered via the keyboard. Every bit a upshot, cyber criminals can become Pin codes and account numbers for e-payment systems, passwords to online gaming accounts, e-mail addresses, user names, email passwords etc.
One time a cyber criminal has got concord of confidential user data, south/he can easily transfer money from the user's account or access the user'due south online gaming account. Unfortunately access to confidential data can sometimes have consequences which are far more than serious than an private's loss of a few dollars. Keyloggers can exist used as tools in both industrial and political espionage, accessing data which may include proprietary commercial information and classified government material which could compromise the security of commercial and land-owned organizations (for example, by stealing individual encryption keys).
Keyloggers, phishing and social engineering (come across 'Computers, Networks and Theft') are currently the chief methods being used in cyber fraud. Users who are aware of security issues can easily protect themselves against phishing by ignoring phishing emails and by non entering any personal information on suspicious websites. Information technology is more than difficult, however, for users to combat keyloggers; the only possible method is to employ an advisable security solution, every bit it's usually impossible for a user to tell that a keylogger has been installed on his/ her automobile.
According to Cristine Hoepers, the manager of Brazil's Figurer Emergency Response Team, which works under the custodianship of the country's Internet Steering Commission, keyloggers have pushed phishing out of first place every bit the most-used method in the theft of confidential data. What's more, keyloggers are becoming more sophisticated – they rails websites visited past the user and only log keystrokes entered on websites of particular interest to the cyber criminal.
In recent years, we take seen a considerable increase in the number of different kinds of malicious programs which have keylogging functionality. No Internet user is immune to cyber criminals, no matter where in the world s/he is located and no matter what organisation southward/he works for.
How cyber criminals use keyloggers
One of the most publicized keylogging incidents recently was the theft of over $1million from client accounts at the major Scandinavian banking concern Nordea. In August 2006 Nordea clients started to receive emails, allegedly from the banking company, suggesting that they install an antispam product, which was supposedly attached to the bulletin. When a user opened the file and downloaded it to his/ her estimator, the machine would be infected with a well known Trojan chosen Haxdoor. This would be activated when the victim registered at Nordea'south online service, and the Trojan would display an error notification with a request to re-enter the registration data. The keylogger incorporated in the Trojan would record information entered past the bank'southward clients, and later send this data to the cyber criminals' server. This was how cyber criminals were able to admission client accounts, and transfer money from them. Co-ordinate to Haxdoor's author, the Trojan has besides been used in attacks against Australian banks and many others.
On January 24, 2004 the notorious Mydoom worm caused a major epidemic. MyDoom broke the record previously ready by Sobig, provoking the largest epidemic in Internet history to date. The worm used social engineering methods and organized a DoS attack on www.sco.com; the site was either unreachable or unstable for several months as a result. The worm left a Trojan on infected computers which was subsequently used to infect the victim machines with new modifications of the worm. The fact that MyDoom had a keylogging function to harvest credit menu numbers was not widely publicized in the media.
In early 2005 the London police prevented a serious attempt to steal cyberbanking information. After attacking a banking arrangement, the cyber criminals had planned to steal $423 million from Sumitomo Mitsui'due south London-based offices. The master component of the Trojan used, which was created by the 32-twelvemonth-old Yeron Bolondi, was a keylogger that immune the criminals to track all the keystrokes entered when victims used the bank's client interface.
In May 2005 a married couple was arrested in London who were charged with developing malicious programs that were used past some Israeli companies in industrial espionage. The calibration of the espionage was shocking: the companies named by the Israeli authorities in investigative reports included cellular providers similar Cellcom and Pelephone, and satellite television provider Yeah. Co-ordinate to reports, the Trojan was used to access information relating to the PR agency Rani Rahav, whose clients included Partner Communications (Israel'due south 2nd leading cellular services provider) and the HOT cable television group. The Mayer company, which imports Volvo and Honda cars to Israel, was suspected of committing industrial espionage confronting Champion Motors, which imports Audi and Volkswagen cars to the country. Ruth Brier-Haephrati, who sold the keylogging Trojan that her husband Michael Haephrati created, was sentenced to four years in jail, and Michael received a two-year sentence.
In February 2006, the Brazilian police arrested 55 people involved in spreading malicious programs which were used to steal user data and passwords to banking systems. The keyloggers were activated when the users visited their banks' websites, and secretly tracked and afterwards sent all information entered on these pages to cyber criminals. The total amount of coin stolen from 200 client accounts at half-dozen of the country'south banks totaled $4.7million.
At approximately the same time, a similar criminal group made upwards of young (20 – 30 twelvemonth old) Russians and Ukrainians was arrested. In tardily 2004, the group began sending banking clients in France and a number of other countries email letters that contained a malicious program – namely, a keylogger. Furthermore, these spy programs were placed on specially created websites; users were lured to these sites using classic social engineering methods. In the same way as in the cases described above, the plan was activated when users visited their banks' websites, and the keylogger harvested all the information entered by the user and sent information technology to the cyber criminals. In the course of xi months over one million dollars was stolen.
There are many more examples of cyber criminals using keyloggers – almost financial cybercrime is committed using keyloggers, since these programs are the most comprehensive and reliable tool for tracking electronic information.
Increased use of keyloggers by cyber criminals
The fact that cyber criminals choose to use keyloggers fourth dimension and again is confirmed past Information technology security companies.
One of VeriSign's recent reports notes that in recent years, the visitor has seen a rapid growth in the number of malicious programs that have keylogging functionality.
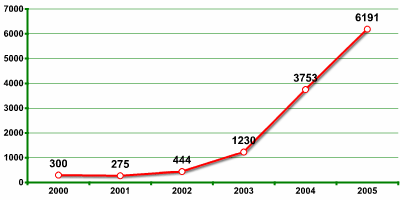
Source: iDefense, a VeriSign Company
One report issued past Symantec shows that almost 50% of malicious programs detected past the company's analysts during the past year practice non pose a direct threat to computers, but instead are used by cyber criminals to harvest personal user information.
According to research conducted past John Bambenek, an analyst at the SANS Institute, approximately ten million computers in the US alone are currently infected with a malicious program which has a keylogging part. Using these figures, together with the total number of American users of due east-payment systems, possible losses are estimated to exist $24.3 one thousand thousand.
Kaspersky Lab is constantly detecting new malicious programs which have a keylogging function. One of the first virus alerts on securelist.com, Kaspersky Lab's dedicated malware information site, was published on 15th June 2001. The warning related to TROJ_LATINUS.SVR, a Trojan with a keylogging function. Since so, there has been a steady stream of new keyloggers and new modifications. Kaspersky antivirus database currently comprise records for more than 300 families of keyloggers. This number does non include keyloggers that are part of complex threats (i.e. in which the spy component provides additional functionality).
Most modernistic malicious programs are hybrids which implement many different technologies. Due to this, whatsoever category of malicious program may include programs with keylogger (sub)functionality. The number of spy programs detected by Kaspersky Lab each calendar month is on the increase, and nigh of these programs use keylogging technology.
Keylogger construction
The main thought behind keyloggers is to become in betwixt any two links in the chain of events betwixt when a key is pressed and when information about that keystroke is displayed on the monitor. This can exist achieved using video surveillance, a hardware bug in the keyboard, wiring or the figurer itself, intercepting input/ output, substituting the keyboard driver, the filter commuter in the keyboard stack, intercepting kernel functions by any means possible (substituting addresses in system tables, splicing function code, etc.), intercepting DLL functions in user mode, and, finally, requesting information from the keyboard using standard documented methods.
Experience shows that the more than complex the approach, the less likely it is to exist used in mutual Trojan programs and the more likely it is to be used in especially designed Trojan programs which are designed to steal financial data from a specific visitor.
Keyloggers can be divided into two categories: keylogging devices and keylogging software. Keyloggers which fall into the beginning category are usually small devices that can exist fixed to the keyboard, or placed within a cable or the computer itself. The keylogging software category is made up of dedicated programs designed to track and log keystrokes.
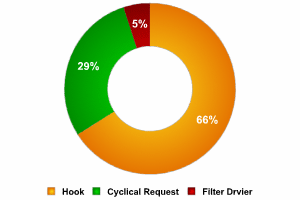
The most common methods used to construct keylogging software are equally follows:
- a arrangement claw which intercepts notification that a primal has been pressed (installed using WinAPI SetWindowsHook for messages sent by the window procedure. Information technology is most often written in C);
- a cyclical data keyboard request from the keyboard (using WinAPI Get(Async)KeyState or GetKeyboardState – most often written in Visual Basic, sometimes in Borland Delphi);
- using a filter driver (requires specialized knowledge and is written in C).
We will provide a detailed explanation of the unlike ways keyloggers are constructed in the second one-half of this article (to be published in the nearly future). But first, here are some statistics.
A rough breakdown of the dissimilar types of keyloggers is shown in the pie nautical chart below:
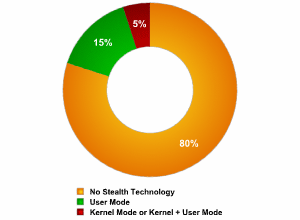
Recently, keyloggers that disguise their files to keep them from beingness found manually or by an antivirus program have get more numerous. These stealth techniques are called rootkit technologies. There are 2 main rootkit technologies used past keyloggers:
- masking in user mode;
- masking in kernel way.
A crude breakup of the techniques used by keyloggers to mask their activity is shown in the pie chart beneath:
How keyloggers spread
Keyloggers spread in much the same manner that other malicious programs spread. Excluding cases where keyloggers are purchased and installed by a jealous spouse or partner, and the apply of keyloggers by security services, keyloggers are mostly spread using the post-obit methods):
- a keylogger can be installed when a user opens a file fastened to an email;
- a keylogger can be installed when a file is launched from an open-admission directory on a P2P network;
- a keylogger can be installed via a web page script which exploits a browser vulnerability. The plan will automatically be launched when a user visits a infected site;
- a keylogger can exist installed by another malicious program already nowadays on the victim machine, if the plan is capable of downloading and installing other malware to the system.
How to protect yourself from keyloggers
Nearly antivirus companies have already added known keyloggers to their databases, making protecting against keyloggers no different from protecting against other types of malicious program: install an antivirus product and keep its database up to engagement. However, since nearly antivirus products classify keyloggers as potentially malicious, or potentially undesirable programs, users should ensure that their antivirus product will, with default settings, discover this blazon of malware. If not, then the production should be configured accordingly, to ensure protection against most common keyloggers.
Allow'south have a closer expect at the methods that tin can be used to protect against unknown keyloggers or a keylogger designed to target a specific organization.
Since the primary purpose of keyloggers is to become confidential information (bank menu numbers, passwords, etc.), the most logical ways to protect against unknown keyloggers are every bit follows:
- using former passwords or two-step hallmark,
- using a system with proactive protection designed to detect keylogging software,
- using a virtual keyboard.
Using a one-time countersign can aid minimize losses if the countersign you enter is intercepted, as the password generated can be used one time only, and the period of time during which the password tin can be used is limited. Even if a sometime countersign is intercepted, a cyber criminal volition not be able to use it in lodge to obtain admission to confidential information.
In order to go i-fourth dimension passwords, yous tin use a special device such equally:
- a USB key (such every bit Aladdin eToken NG OTP (folio in Russian)):

- a 'calculator' (such equally RSA SecurID 900 Signing Token):

In order to generate 1-time passwords, you lot can as well use mobile phone text messaging systems that are registered with the banking organization and receive a PIN-code equally a reply. The PIN is then used together with the personal code for authentication.
If either of the higher up devices is used to generate passwords, the procedure is as described below:
- the user connects to the Cyberspace and opens a dialogue box where personal data should be entered;
- the user so presses a push button on the device to generate a one-time countersign, and a password will announced on the device's LCD display for fifteen seconds;
- the user enters his user proper noun, personal Pin lawmaking and the generated one-time password in the dialogue box (normally the Pin code and the primal are entered 1 later the other in a single pass code field);
- the codes that are entered are verified by the server, and a decision is made whether or not the user may admission confidential data.
When using a calculator device to generate a countersign, the user will enter his Pivot code on the device 'keyboard' and press the ">" push.
Quondam password generators are widely used past banking systems in Europe, Asia, the US and Australia. For example, Lloyds TSB, a leading banking company, decided to use password generators back in November 2005.
In this case, withal, the company has to spend a considerable amount of money equally information technology had to acquire and distribute password generators to its clients, and develop/ purchase the accompanying software.
A more cost efficient solution is proactive protection on the client side, which can warn a user if an attempt is fabricated to install or activate keylogging software.
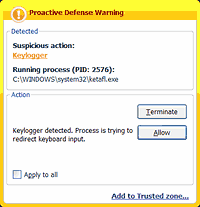
Proactive protection against keyloggers in
Kaspersky Internet Security
The principal drawback of this method is that the user is actively involved and has to determine what action should exist taken. If a user is not very technically experienced, s/he might make the wrong decision, resulting in a keylogger being allowed to bypass the antivirus solution. Nevertheless, if developers minimize user involvement, then keyloggers will be able to evade detection due to an insufficiently rigorous security policy. Yet, if settings are besides stringent, and then other, useful programs which contain legitimate keylogging functions might also be blocked.
The final method which tin can be used to protect against both keylogging software and hardware is using a virtual keyboard. A virtual keyboard is a program that shows a keyboard on the screen, and the keys can exist 'pressed' by using a mouse.
The idea of an on-screen keyboard is nothing new – the Windows operating system has a born on-screen keyboard that tin exist launched as follows: Offset > Programs > Accessories > Accessibility > On-Screen Keyboard.
An case of the Windows on-screen keyboard
However, on-screen keyboards aren't a very popular method of outsmarting keyloggers. They were non designed to protect against cyber threats, but as an accessibility tool for disabled users. Information entered using an on-screen keyboard can hands be intercepted by a malicious program. In order to be used to protect against keyloggers, on-screen keyboards take to be specially designed in order to ensure that data entered or transmitted via the on-screen keyboard cannot be intercepted.
Conclusions
This commodity has provided an overview of how keyloggers – both keylogging software and hardware – office and are used.
- Even though keylogger developers market their products as legitimate software, most keyloggers can be used to steal personal user data and in political and industrial espionage.
- At present, keyloggers – together with phishing and social engineering methods – are one of the most commonly used methods of cyber fraud.
- It security companies have recorded a steady increase in the number of malicious programs that accept keylogging functionality.
- Reports prove that there is an increased tendency to employ rootkit technologies in keylogging software, to help the keylogger evade manual detection and detection past antivirus solutions.
- Only defended protection tin observe that a keylogger is being used for spy purposes.
- The following measures can exist taken to protect against keyloggers:
- use a standard antivirus that tin can be adjusted to detect potentially malicious software (default settings for many products);
- proactive protection will protect the system against new ,modifications of existing keyloggers;
- use a virtual keyboard or a system to generate one-time passwords to protect confronting keylogging software and hardware.
Keyloggers: Implementing keyloggers in Windows. Part Ii
Source: https://securelist.com/keyloggers-how-they-work-and-how-to-detect-them-part-1/36138/
Posted by: abramsinualst.blogspot.com


0 Response to "How To Find If Keylogger Is Installed On Computer"
Post a Comment